Secure Copy Protocol (SCP) is a vital tool for transferring files securely between systems. However, capturing and logging its output can be challenging due to its dynamic nature. This guide will walk you through various methods to effectively capture and log SCP output, helping you monitor, troubleshoot, and audit your file transfers with ease.
Understanding SCP and Its Output
Secure Copy Protocol (SCP) is a network protocol that allows for secure file transfers between a local and remote host, or between two distant hosts. It communicates over SSH (safe Shell), using the same authentication and security methods to ensure safe data transmission.
When using SCP, it typically generates two types of output:
- Progress Information: This includes real-time details such as the speed of the transfer, the percentage of the file that has been transferred, and an estimate of how much time remains until the transfer is complete. This information helps monitor the progress of file transfer and ensures that everything is moving as expected.
- Error Messages: Error messages provide feedback when something goes wrong during the transfer process, such as network outages, permission issues, or connection dropouts. They are critical for troubleshooting since they explain what went wrong and how to solve it.
Capturing this output is crucial for several reasons:
- Troubleshooting transfer issues: If a file transfer fails, the output logs can provide detailed information about what went wrong, allowing you to resolve the problem efficiently.
- Auditing file transfer activities: Keeping a log of SCP output helps maintain a record of file transfers, which can be useful for auditing and compliance purposes.
- Monitoring transfer performance: By analyzing the output, you can monitor transfer speeds and performance, helping you optimize your file transfer processes.
- Automating responses to specific events or errors: Capturing SCP output allows you to automate responses to specific conditions, such as retrying a failed transfer or triggering alerts.
The challenge in capturing SCP output lies in its dynamic nature—the progress bar updates continuously, making it difficult to capture using standard output redirection techniques.
Quick Guide: Capturing SCP Output
Capturing SCP output can help you monitor, troubleshoot, and analyze your file transfers. Here are some quick and effective methods:
Use the
scriptcommand to record the entire terminal session: This method records your entire terminal session, capturing all output generated by the SCP command.script -c \ "scp -i /path/to/private/key /path/to/source/file \ username@remote-server:/path/to/destination/" output.txtFor example:
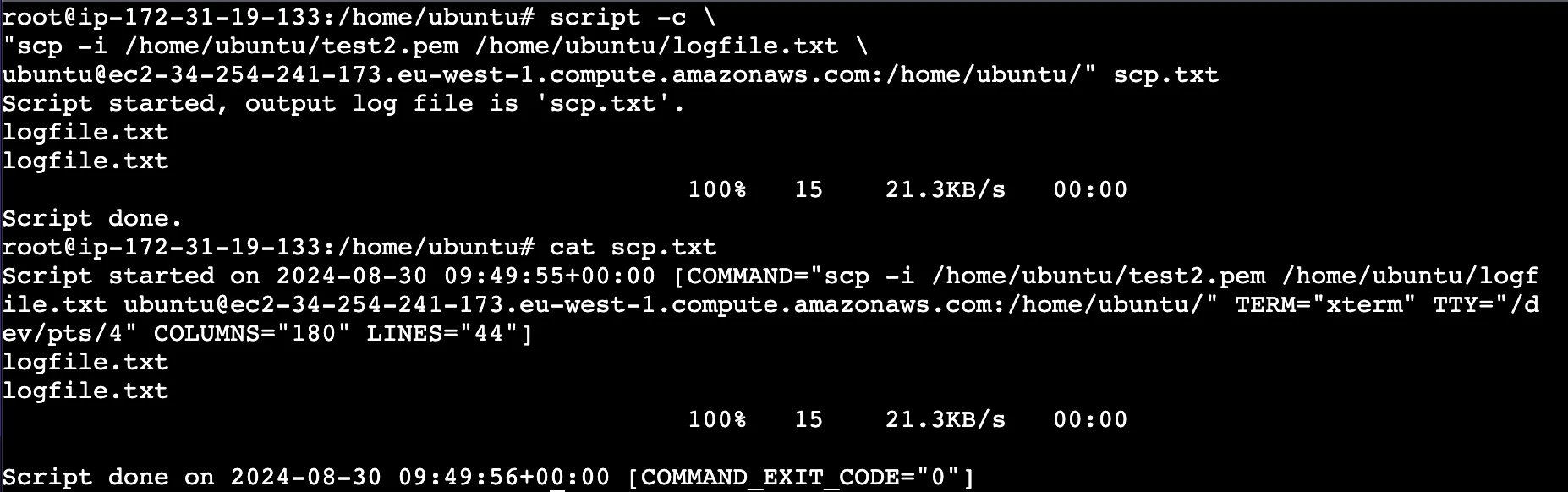
Using the script command The above command executes an SCP operation to copy
logfile.txtfrom one server to another. Thescriptcommand records the output of this SCP operation, displays the output in the terminal, and saves this output to a local file calledscp.txt.Redirect SCP output to a file: This technique redirects both standard output and error messages to a file while displaying them on your terminal.
scp /path/to/source /path/to/destination 2>&1 | tee logfile.txtUtilize SCP's verbose mode: Verbose mode provides detailed information about the transfer process, which is useful for debugging.
scp -v /path/to/source /path/to/destination 2>&1 | tee logfile.txtCombine methods for comprehensive capture: By combining the
scriptcommand with verbose mode and output redirection, you can capture the most detailed log of your SCP session.script -c "scp -v /path/to/source /path/to/destination 2>&1 | tee logfile.txt" session_log.txt
Each method has its strengths, depending on your needs, and in the detailed sections, you’ll learn the pros and cons of each approach.
Detailed Methods for Capturing SCP Output
Using the script Command
The script command is a handy tool in Unix-like systems that records everything displayed on your terminal during a session. This can be incredibly useful for capturing SCP output, especially when you want to log the entire process, including dynamic elements like the progress bar.
Start the script:
script <filename>For example:
script logfile.txtThis command starts recording everything that appears in your terminal and saves it to
logfile.txt.Run your SCP command: Run your SCP command as you normally would. The progress information, error messages, and everything else will be captured in the
logfile.txt.scp /path/to/source /path/to/destinationExit the script session: Type
exitto stop the script session. The complete log of your terminal session, including the SCP command, is now saved.exit
Advantages:
- Complete Capture:
Scriptcaptures all terminal output, making it ideal for logging not just the SCP output, but also any commands you might run during the session. - Accuracy: It preserves the exact format of the output, including dynamic elements like the progress bar, which can be difficult to capture using standard output redirection.
Limitations:
- Verbose Logs: The log file includes everything that happens in the terminal, not just the SCP output. This can make the log file large and harder to parse if you only need specific information.
- Resource Usage: Recording a terminal session, especially for large file transfers, can be resource-intensive, potentially slowing down your system.
After capturing the output, use tools like grep or awk to extract specific information. For example, if you only want to see the transfer summaries, you can use:
grep "Transferred" logfile.txt
Redirecting SCP Output
Output redirection in Unix-like systems allows you to capture the output of commands, including SCP (Secure Copy Protocol), for monitoring, logging, and troubleshooting. To capture both standard output (stdout) and error output (stderr) when running SCP, you can use the following command:
scp /path/to/source /path/to/destination 2>&1 | tee logfile.txt
- The
2>&1part redirects error messages (which usually go to stderr) to the same stream as regular output (stdout). This ensures that all output, including errors, is captured together. - The
tee logfile.txtcommand displays the output on the console while simultaneously writing it to a file (logfile.txt). This is useful for real-time monitoring while also keeping a log for later review.
Advantages:
- Redirecting SCP output ensures that all the data generated during the transfer, including both standard output and error messages, is captured in a single log file. This is particularly beneficial for monitoring and troubleshooting, as it allows you to have a complete record of the transfer process. For example, if an error occurs, you can easily refer to the log to see what went wrong without missing any details.
- The use of the tee command allows you to monitor the SCP transfer in real-time while simultaneously logging the output. This dual capability means you can observe the progress directly on your terminal, which is helpful for large or critical transfers where real-time feedback is essential. At the same time, all this information is stored in a log file for future reference, enabling you to review the entire process afterward.
Limitations:
- SCP’s progress bar is dynamic, meaning it continuously updates on the same line as the transfer progresses.
- This behavior can lead to challenges when capturing output in a log file. The progress bar might not be recorded accurately because it’s designed to refresh the display rather than generate new lines of output.
- As a result, the log file could show garbled or incomplete progress information, making it difficult to track the precise status of the transfer from the logs alone. This limitation is particularly noticeable in long transfers where continuous monitoring of progress is important.
Leveraging SCP's Verbose Mode
Verbose mode in SCP, enabled with the -v option, provides a detailed account of the entire file transfer process. This mode is particularly useful when you need to gain deeper insights into how the transfer is progressing and to diagnose any issues that might arise.
Here's how you can use it:
scp -v /path/to/source /path/to/destination 2>&1 | tee logfile.txt
Benefits of verbose mode:
- In-Depth Diagnostics: Verbose mode is invaluable for troubleshooting. It provides you with granular details about every step of the file transfer, which can help you pinpoint where a transfer might be failing. For instance, if there’s a problem with the SSH connection or file permissions, the verbose output will highlight exactly where and why the issue is occurring. This makes it much easier to identify and fix problems quickly, without having to guess or rely on less detailed error messages.
- Debugging: The verbose output often includes lines that start with "debug," which offers deep insights into the SSH connection and file transfer. These debug messages are particularly useful for diagnosing complex issues that go beyond simple connection problems.
- For example, if there’s an issue with SSH key authentication or with the way SCP is handling the connection, these debug lines can provide the necessary clues to resolve the issue. This level of debugging information is crucial for system administrators and developers who need to ensure reliable file transfers in their workflows.
When interpreting verbose output, look for lines starting with "debug1" for detailed information about the connection and transfer process.
Advanced Techniques for Logging SCP Output
Custom Shell Scripts for Automated Logging
Create a shell script to automate the logging process: Save the following code as
scp_log.sh#!/bin/bash log_file="/path/to/scp_log_$(date +%Y%m%d_%H%M%S).txt" scp -v "$1" "$2" 2>&1 | tee "$log_file"The above script does the following:
- Defines
log_filewith a filename that includes a timestamp, ensuring unique log files for each execution. - Runs the
scpcommand in verbose mode (v), capturing both standard output and error streams. - Pipes the combined output to
tee, which writes it to the specified log file while also displaying it in the terminal.
Make the Script Executable:
Run the following command to make the script executable:
chmod +x scp_log.shUse the Script: Execute the script with the source and destination paths as arguments:
./scp_log.sh /path/to/source /path/to/destinationThis will start the SCP transfer and log all output, including detailed information about the transfer process, to a timestamped log file.
Using tee for Simultaneous Display and Logging
The tee command allows you to view output in real-time while saving it to one or more files. This is useful for monitoring the SCP transfer as it happens and keeping a record of the full output. Here’s how you can use tee for this purpose:
scp /path/to/source /path/to/destination 2>&1 | tee >(grep "Transferred" >> transfer_summary.log) full_log.txt
This command achieves the following:
- Displays Full Output: The
scpcommand's full output is displayed in the terminal, so you can monitor the transfer as it progresses. - Saves Complete Output: The full output is also saved to
full_log.txt, allowing you to review all details later. - Extracts Transfer Summaries: The output is filtered with
grepto extract lines containing "Transferred" and appends these summaries totransfer_summary.log. This is useful for quick insights into the transfer status without needing to sift through the entire log file.
Implementing Log Rotation
When using SCP frequently, the log files can quickly become large and unmanageable. To address this, you can implement log rotation, which automatically manages log file sizes by rotating, compressing, and deleting old logs. Here's how to set it up:
If
logrotateis not already installed on your system, you can install it using your package manager. For example, on a Debian-based system, use:sudo apt-get install logrotateCreate a configuration file: Set up a configuration file for your SCP logs at
/etc/logrotate.d/scp_logs. This file will telllogrotatehow to manage your log files./path/to/scp_logs/*.log { rotate 7 daily compress missingok notifempty }
With this configuration, your SCP logs will be automatically rotated every day, and only the last 7 days' logs will be kept. Older logs will be compressed to save space, ensuring that your log directory remains organized and manageable.
Parsing SCP Logs with awk and sed
Once you have SCP logs, you may want to extract specific information for analysis. Tools like awk and sed are powerful for this purpose:
Extracting Transfer Speeds with
awk: If your SCP logs contain lines that show transfer speeds, you can useawkto extract this data.awk '/Transferred/ {print $10}' scp_log.txtThis command looks for lines containing the word "Transferred" and prints the 10th field, which might represent the transfer speed.
Filtering Error Messages with
sedandgrep: You can usesedto filter out unwanted lines orgrepto search for specific error messages.# Extract error messages sed -n '/^debug1/!p' scp_log.txt | grep -i errorThis command searches for lines containing "error" (case-insensitive) and excludes lines starting with "debug1," focusing on relevant error messages.
Troubleshooting Common SCP Output Capture Issues
Capturing SCP output can be difficult at times owing to a variety of circumstances, including the progress bar's fluid character, huge file transfers, authorisation concerns, and network problems. Here's a quick approach to resolving some typical issues:
Dealing with Progress Bar Interference
The SCP progress indicator refreshes repeatedly on the same line, which might interfere with log collection and result in incomplete or garbled logs.
Solutions:
- Use the
q(quiet) Option:Run SCP with the
qoption to suppress the progress meter. This prevents the progress bar from cluttering the output, making it easier to log:scp -q /path/to/source /path/to/destinatio 2>&1 | tee logfile.txt
- Employ
scriptortee:Use the
scriptcommand to capture the entire terminal session, including the dynamic progress bar:script -c "scp /path/to/source /path/to/destination" logfile.txtAlternatively, use
teeto capture and display the output simultaneously:scp /path/to/source /path/to/destination 2>&1 | tee logfile.txtWhile
teewon’t solve progress bar interference, it ensures you capture all output in real-time.
Handling Large File Transfers
Large file transfers can create exceptionally large log files, which might be difficult to manage and analyze.
Solutions:
- Use
tail -ffor Real-Time Monitoring:Monitor the log file in real-time using
tail -f:tail -f logfile.txtThis command displays new log entries as they are written, allowing you to track transfer progress live.
- Implement Log Rotation:
- Use tools like
logrotateto manage log file sizes by rotating and compressing old logs. This ensures log files don’t grow too large:Create a logrotate configuration file (e.g.,
/etc/logrotate.d/scp_logs):/path/to/scp_logs/*.log { rotate 7 daily compress missingok notifempty }This setup rotates logs daily, keeps the last 7 days of logs, and compresses older logs to save space.
- Use tools like
- Consider
rsyncwith--progress:For detailed transfer information and better control, use
rsyncinstead of SCP. The--progressoption provides a detailed progress report:rsync --progress source destination
Addressing Permission-Related Logging Problems
Permissions issues can prevent logging processes from creating or writing to log files.
Solutions:
- Run SCP with
sudoif Necessary:If you encounter permission errors, try running the SCP command with
sudoto ensure it has the necessary permissions:sudo scp source destination 2>&1 | tee logfile.txt
- Check and Set Correct Permissions:
Ensure that the directories and files used for logging have appropriate permissions. Set permissions using
chmod:chmod 755 /path/to/log_directory chmod 644 /path/to/logfile.txt
Resolving Network-Related Output Capture Issues
Network issues can cause interruptions or incomplete transfers, affecting log capture.
Solutions:
- Use the
COption with SCP:Enable compression with the
Coption to potentially improve transfer speeds and reduce the likelihood of network interruptions:scp -C source destination 2>&1 | tee logfile.txt
- Implement Retry Logic:
Add retry logic to your scripts to handle network interruptions gracefully. For example:
#!/bin/bash for i in {1..5}; do scp source destination && break || sleep 10 doneThis script attempts the SCP transfer up to 5 times, waiting 10 seconds between attempts if it fails.
By addressing these common issues with the outlined solutions, you can effectively capture and manage SCP output, ensuring a smoother file transfer experience.
Monitoring Logs with SigNoz
To effectively monitor Logs, using an advanced observability platform like SigNoz can be highly beneficial. SigNoz is an open-source observability tool that provides end-to-end monitoring, troubleshooting, and alerting capabilities for your applications and infrastructure.
- Create a SigNoz Cloud Account
SigNoz Cloud provides a 30-day free trial period. This demo uses SigNoz Cloud, but you can choose to use the open-source version.
SigNoz cloud is the easiest way to run SigNoz. Sign up for a free account and get 30 days of unlimited access to all features.
You can also install and self-host SigNoz yourself since it is open-source. With 19,000+ GitHub stars, open-source SigNoz is loved by developers. Find the instructions to self-host SigNoz.
- Create a Sample Log File
As an example, you can create a sample log file called app.log with the following dummy data:
This is log line 1
This is log line 2
This is log line 3
This file represents a log file of your application. You can choose any file that contains your application's log entries.
- Download the OpenTelemetry Collector
The OpenTelemetry collector provides a vendor-neutral way to collect, process, and export your telemetry data such as logs, metrics, and traces.
Follow this guide to download and extract the OpenTelemetry Collector on your machine, but stop after the extraction step. Ensure you download the latest version available.
- Setup the Otel Collector
Create a config.yaml file in the otelcol-contrib folder and paste the below content in it:
receivers:
filelog/app:
include: [ /tmp/app.log ] #include the full path to your log file
processors:
batch:
send_batch_size: 1000
timeout: 10s
exporters:
otlp:
endpoint: "ingest.{region}.signoz.cloud:443"
tls:
insecure: false
headers:
"signoz-access-token": "<SIGNOZ_INGESTION_KEY>"
logging:
verbosity: normal
service:
pipelines:
logs:
receivers: [filelog/app]
processors: [batch]
exporters: [otlp, logging]
The above configuration uses the filelog receiver to collect logs from the specified log file, process them in batches, and export them to SigNoz for monitoring using the OTLP protocol.
Replace SIGNOZ_INGESTION_KEY and {region}with the values specific to your SigNoz cloud account.
- Run the Collector Service
To run the collector service, navigate to the otelcol-contrib folder and run the below command:
./otelcol-contrib --config ./config.yaml
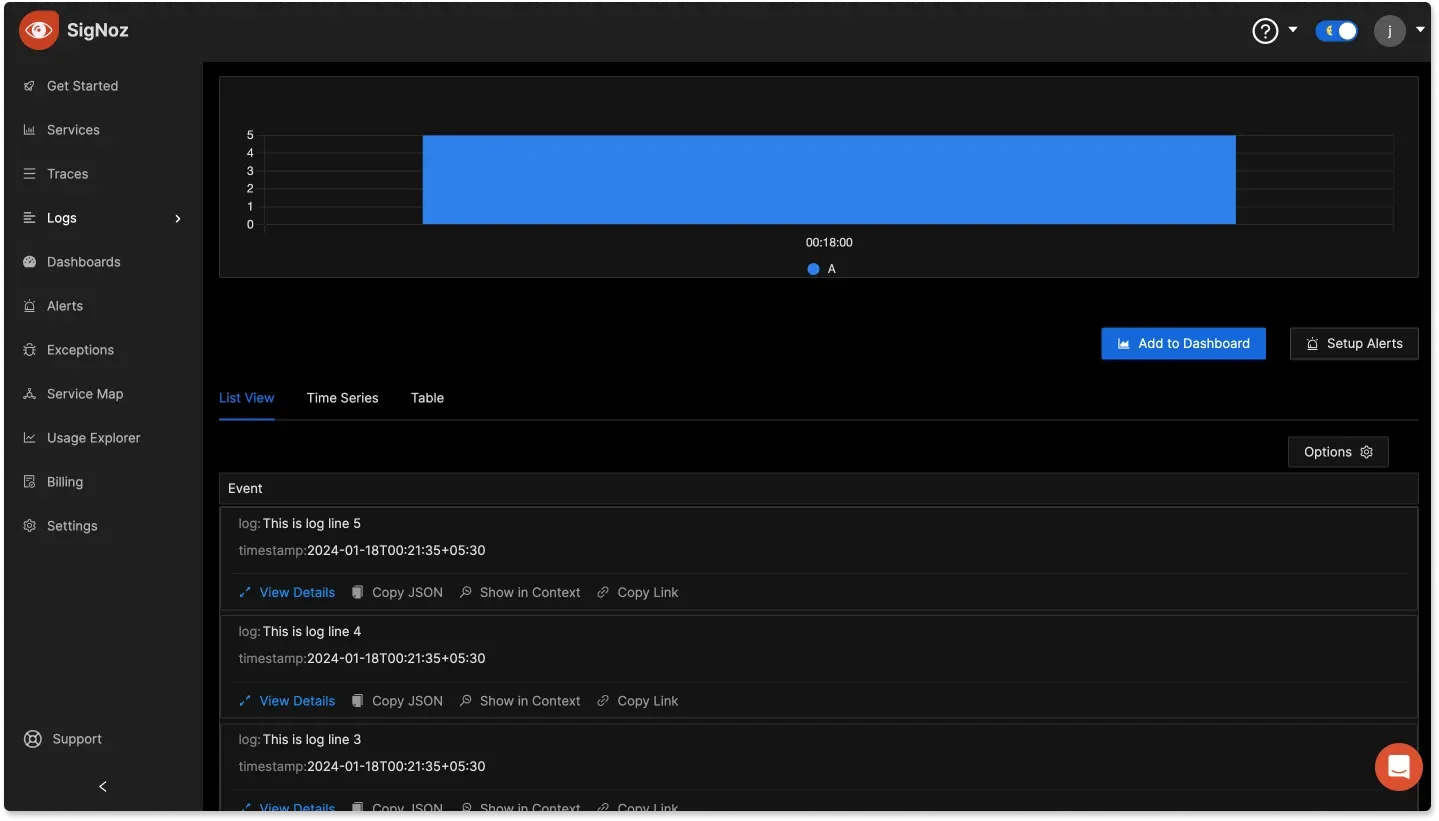
The logs will be sent to your SigNoz account. You can view them on the “Logs” page.
Best Practices for SCP Output Management
Here are some best practices to follow in managing SCP outputs:
- Establish consistent logging conventions:
- Use a consistent format for your log files and a clear naming system. For example, always include the date and the type of transfer in the filename. This makes it easier to find and understand your logs quickly.
- Include the time when each log entry was made and any unique identifiers for the transfers. This helps you track when things happened and link specific log entries to particular file transfers.
- Implement secure log storage and access control:
- To protect your logs, encrypt them. This entails converting your log data into a code that only authorized users can see, so protecting sensitive information from unauthorized access.
- Allow just specified personnel to read or manage your log files. This guarantees that only authorized workers have access to the logs, lowering the risk of data breaches or unauthorized changes.
- Conduct regular log analysis:
- Set up automated systems to regularly check your logs for issues. This can help you spot problems or trends without having to manually review every log entry.
- Employ sophisticated tools like SigNoz or ELK Stack to analyze your logs in-depth. These tools can provide detailed insights and visualizations, helping you understand performance issues or other problems more clearly.
- Integrate SCP logs with broader system monitoring:
- Connect your SCP logs with other system performance data. This helps you see how file transfers affect the overall system and identify any issues that might be impacting performance.
- Use a centralized logging system to collect logs from different sources, including SCP transfers. This way, you have a single place to monitor and manage all your logs, making it easier to get a complete view of your system’s activities.
Key Takeaways
- SCP transfers can face various problems including network interruptions, connection drops, or file corruption. These issues might be caused by factors such as unstable network conditions, permission errors, or incorrect configurations.
- Different techniques for logging SCP output include using the script command to record the entire terminal session, tee for real-time monitoring and saving of logs, and enabling verbose mode with the -v flag to get detailed transfer information.
- Each method has its benefits: the
scriptcommand captures all terminal activity, theteecommand allows simultaneous display and logging, and the verbose mode provides in-depth details about the transfer process. - To manage SCP output over time, you can use custom shell scripts that automate the logging process, making it easier to handle repetitive tasks. Implementing log rotation helps manage log file sizes and ensures that logs do not consume excessive storage. Log rotation settings can be customized to archive, compress, and delete old logs, keeping the system organized and efficient.
- Capturing SCP output helps you detect these problems by providing detailed information about the transfer process, which is crucial for diagnosing and resolving issues quickly and effectively. SigNoz and similar monitoring tools offer advanced capabilities for analyzing SCP logs
- Consistent analysis and handling of SCP logs is critical for system stability and security. This includes ensuring that logs are securely kept, available for audits, and checked routinely to detect any concerns.
FAQs
Why doesn't standard output redirection work with SCP?
Standard output redirection doesn’t work well with SCP because SCP updates its progress bar in-place using carriage returns, which repeatedly overwrites the same line. This dynamic updating isn't captured properly by standard redirection, resulting in incomplete or garbled logs. To capture SCP’s output effectively, including the progress bar and error messages, use tools like script or tee.
How can I capture SCP output without affecting its progress display?
To capture SCP output without disrupting its progress display, you can use the script command or the tee command combined with process substitution. Here's how:
- Using
script: Thescriptcommand records everything displayed in the terminal:
script -c "scp source destination" logfile.txt
This will capture the SCP output, including the progress display, without affecting the terminal output.
Using
teewith Process Substitution: This method captures the output while still displaying the progress bar:scp source destination 2>&1 | tee logfile.txt
This command allows you to see the progress on the screen while logging the output to a file.
Is it possible to log SCP output for automated transfers?
Yes, you can log SCP output for automated transfers by creating a shell script that wraps the SCP command with logging. This script can then be used in automated processes like cron jobs. Here's a basic example:
#!/bin/bash
log_file="/path/to/scp_log_$(date +%Y%m%d_%H%M%S).txt"
scp "$1" "$2" 2>&1 | tee "$log_file"
What's the best way to analyze large volumes of SCP logs?
The best way to analyze large volumes of SCP logs is to use log analysis tools like SigNoz or the ELK stack for comprehensive, large-scale analysis. For quicker insights, you can use command-line tools like awk, sed, and grep to filter and extract relevant information directly from the logs.